Table of Contents
Remote work is a revolutionary shift that offers businesses some significant advantages like operational cost savings, talent globalization, and workforce flexibility.
However, the perk of remote work often comes along with concerns around compliance risks and security limitations that can significantly hamper business operations, if not dealt with effective measures.
During the COVID pandemic era—when businesses pivoted to remote operations to maintain business continuity and preserve revenue (a necessary and positive step)—global cybersecurity attacks surged by 238%.
“As the lines between work and home have blurred, security risks have soared and everyday actions such as opening an attachment can have serious consequences. Without all of the pre-pandemic sources of visibility of devices, and how they are being used and by who, IT and security teams are working with clouded vision”, says Chief Information Security Officer (CISO) of HP Inc, Joanna Burkey. (The FinTech Times)
Ask any CISO or COO today, who is handling distributed teams, what keeps them up at night, and the answer isn’t just “cybersecurity”, it is also the compliance risk hiding in everyday workflows.
The challenge isn’t a lack of policy. You’ve done the hard work. Your company likely has detailed frameworks for SOC 2, HIPAA, GDPR, or ISO 27001. The issue is that in a remote-first environment, enforcement without visibility is a false sense of security.
Keep reading to learn the 3-step executive playbook to proactively reduce compliance risk in remote teams—without creating a culture of fear or micromanagement.
Whether you’re a CISO trying to fortify security or a COO aiming to streamline operations without friction, you’ll walk away with a tactical framework to:
- Reclaim visibility across your remote environment
- Automate policy enforcement at scale
- Build a culture of trust-powered compliance
Let’s dive in.
Remote Work Is Reshaping the Cybersecurity Landscape
As businesses continue to adopt flexible work models, the pressure to rethink their security posture is also increasing.

Why Remote Work Broke Your Compliance Model
For CISOs and COOs, managing remote compliance is no longer a checklist—it’s a moving battlefield where threats hide in plain sight. A recent OpenVPN survey revealed that 73% of VP and C-suite leaders in the IT industry believe remote operations carry greater security risks than on-site setups.
And rightly so.
Managing a geographically dispersed team introduces serious risks to data security and compliance.
When employees work outside secured office spaces, sensitive business data is exposed—leading to data breaches, unauthorized access, and compliance violations.
But being a compliance-focused leader, the challenge is not just technical; it is also behavioral. Remote employees may leave systems unattended, mishandle data, or become too casual with protocols—raising the risk of cybersecurity attacks and insider threats.
Let’s uncover the common and often overlooked factors that weaken remote compliance:
Regulatory fragmentation: Compliance is not a one-size-fits-all approach, especially when a team is scattered across states and borders. Being responsible for data protection laws (GDPR, HIPAA, etc), labor laws, and tax laws can be complex and come with their own nuances.
Task outsourcing: Delegating your business processes to third-party vendors exposes your sensitive data to them. Neglecting to carefully review third-party vendors’ security measures and data loss prevention (DLP) strategies can lead to accidental data leaks, unauthorized access, and serious compliance breaches — which can ultimately harm your business reputation and customer trust.
Inadequate data security: Many employees operate using outdated or personal devices that lack encryption capabilities, antivirus, patch management, firewall, password policies, access controls, and other security-focused system integrities. Moreover, using public Wi-Fi or unsecured home networks can also impact data security.

Take Control of Productivity, Security, and Compliance—All in One Platform
Perform company-wide system audits
Get accurate reports on software & hardware health
Improve compliance and operational security effortlessly
Monitoring gaps: You can’t protect what you can’t see. Without physical oversight or the right employee monitoring tools, it becomes nearly impossible to identify non-compliant behavior, unusual activities, internal fraud, or policy violations that your employees can perform.
Training deficiencies: Without regular compliance-focused training, employees will lack basic awareness and protocols on how to handle sensitive data in remote setups. Unclear policies, misunderstanding security risks, or failure to recognizing potential threats leads to increased chances of data breaches and regulatory violations in your business.
Cloud and VPN vulnerabilities: In remote setups, misconfigured cloud storage or overloaded VPNs are frequent, leaving private information vulnerable to illegal access or interception. Many companies switch to remote operations without strengthening their digital infrastructure.
Physical security threats: The misplacement or theft of computer systems can create unnecessary struggles—not only will it lead to sensitive data theft, but it will also result in the loss of IT infrastructure.
Shadow IT: It becomes difficult to know if remote employees are using any unverified software that may contain viruses or threats, which can cause data leaks. Every unsanctioned app is a compliance time bomb, creating data exposure without IT knowing it.

Download Free Remote Compliance Assessment Checklist for CISOs & COOs
An Actionable 3-Step Playbook for CISOs and COOs
Regardless of which industry, location, or business you are in, you will have to follow certain compliance regulations. If we go into the detailing of every compliance, it will become complicated. But the essence of almost every compliance is the same: security of data, safeguarding public privacy and data, and taking full ownership in case of any mishappening or wrongdoing.
Here is a 3-step practical, research-backed, and actionable guide for CISOs, COOs, or any other compliance-focused leaders who want to minimize compliance risks in remote operations without adding much to the operational overhead.
Read more: How to Enforce a Clean Desk Policy in Your Business in 2025: A Comprehensive Guide
Step 1: Visibility Is the Foundation—Build a 360° Monitoring Framework
When it comes to compliance protection, you can’t safeguard what you can’t see. Implementing monitoring tools in your operations helps you track, manage, and optimize your security efforts from anywhere. By monitoring both computer systems and end-user activities, managers can understand how their company’s sensitive data is being handled at every moment—helping them to improve their risk mitigation and incident response strategies. With continuous monitoring, you can spot data breaches before they happen and take proactive measures, helping you minimize compliance and data risks.
Incorporating tools like employee monitoring or compliance monitoring, you can effortlessly comply with enterprise-grade regulations (GDPR, HIPAA, ISO, SOC, etc), along with generating audit trials to strengthen accountability. With detailed logs and activity data in place, teams can trace incidents faster, understand what went wrong, and take corrective actions. Regular audits backed by these insights make it easier to stay aligned with internal policies and meet external compliance requirements.
Here’s a tactical visibility model to adopt:
Device-Level Monitoring (DLM):
Track what devices are being used, who owns them, and whether they meet compliance standards (e.g., encryption, antivirus, policy updates).
User Behavior Analytics (UBA):
Use AI-powered systems to flag abnormal behavior—like excessive file access, after-hours logins, or unusual app usage.
Contextual Screen Monitoring:
Go beyond snapshots. Implement smart screen recording tools that detect and flag policy violations (e.g., viewing sensitive data in public, opening personal emails alongside work dashboards).
Location & Network Tagging:
Understand where work is being done. Enforce location-aware policies—like blocking access from certain geographies or insecure networks.
Custom Risk Dashboards for Leadership:
COOs and CISOs shouldn’t rely on bloated reports. Create real-time dashboards that surface only the most critical risks and trend deviations.
Step 2: Automate Compliance Controls—Because Manual Enforcement Won’t Scale
The next move for CISOs and COOs is to automate their compliance control. Manual compliance checks are for small workforces (generally between 11 to 50). But when you are a team of 100 or 1000, even distributed across different time zones and geographies, it becomes burdensome, error-prone, and budget-draining to scale headcount for conducting compliance checkups. It’s not even sustainable if you keep on scaling.
Moreover, remote and hybrid setups have made it nearly impossible to enforce compliance policies with the help of traditional means like checklists, reminders, or training alone.
Automation doesn’t just minimize errors—it increases consistency, accountability, and speed in your security strategies. You can’t monitor every single action of your team members, but you can easily set intelligent guardrails that silently work in the background.
Key Areas Where Automation Delivers Massive Impact:
Access Control Enforcement:
Automatically restrict or revoke access based on role, device, location, or compliance status (e.g., blocking file downloads from personal devices or unknown IPs).
Real-Time Data Redaction & Masking:
Auto-mask sensitive data fields (PII, PHI, financial data) during screen sharing or while working on public-facing tools.
Violation Detection & Alerts:
Set predefined triggers that detect risky behavior (like external file transfers, screenshot attempts, or use of unsanctioned tools) and send instant alerts—or even lock access.
Activity-Based Policy Triggers:
For example, if an employee logs in from an unsecured network or a new geography, they automatically enforce VPN usage, restrict certain tools, or require multi-factor authentication.
Automated Reporting & Audit Logs:
Ensure every action is recorded and available for audit trails—without burdening your team with manual documentation.
Step 3: Turn Compliance Into a Culture—Train, Test, and Enforce with Empathy
Technology helps you to enforce rules, but a culture helps you to sustain them.
The Thomson Reuters Risk & Compliance Survey Report revealed that a poor company culture is among the top three reasons that becomes a hindrance for the team to address compliance risks effectively. Therefore, in remote setups, adaptable culture becomes your superpower. It encourages employees to understand the high stakes of compliance risks and make them feel accountable, so they treat security protocols as checkboxes, not critical responsibilities.
Here’s how executive leaders can make the cultural shift that supports compliance safety:
Communicate the ‘Why’ Frequently, Not Just the ‘What’:
Don’t just tell employees what to do, rather, explain why it matters. Use real stories of breaches, fines, or industry failures to show the cost of non-compliance.
Make Security Personal:
Connect compliance with individual responsibility. Highlight how one careless moment—like a screenshot, unvetted app, or unsecured login—can affect not just the company, but their own credibility and trust.
Recognize & Reward Secure Behavior:
Don’t only flag violations—celebrate compliance champions. Highlight teams or individuals who follow best practices and encourage others to follow suit.
Create Feedback Loops with Employees:
Involve team members in refining compliance processes. What feels frustrating? Where are the blockers? When people feel heard, they participate in the process.
Train Continuously, Not Just During Onboarding:
The compliance awareness part can be discussed in monthly team meetings or standups. Use micro-learning, simulations, or short refresher videos to keep it front of mind.

Discover How CISOs & COOs Use wAnywhere to Automate Compliance in Remote Teams
Leverage AI-powered visibility, real-time threat detection, and audit-ready logs—purpose-built for remote operations.
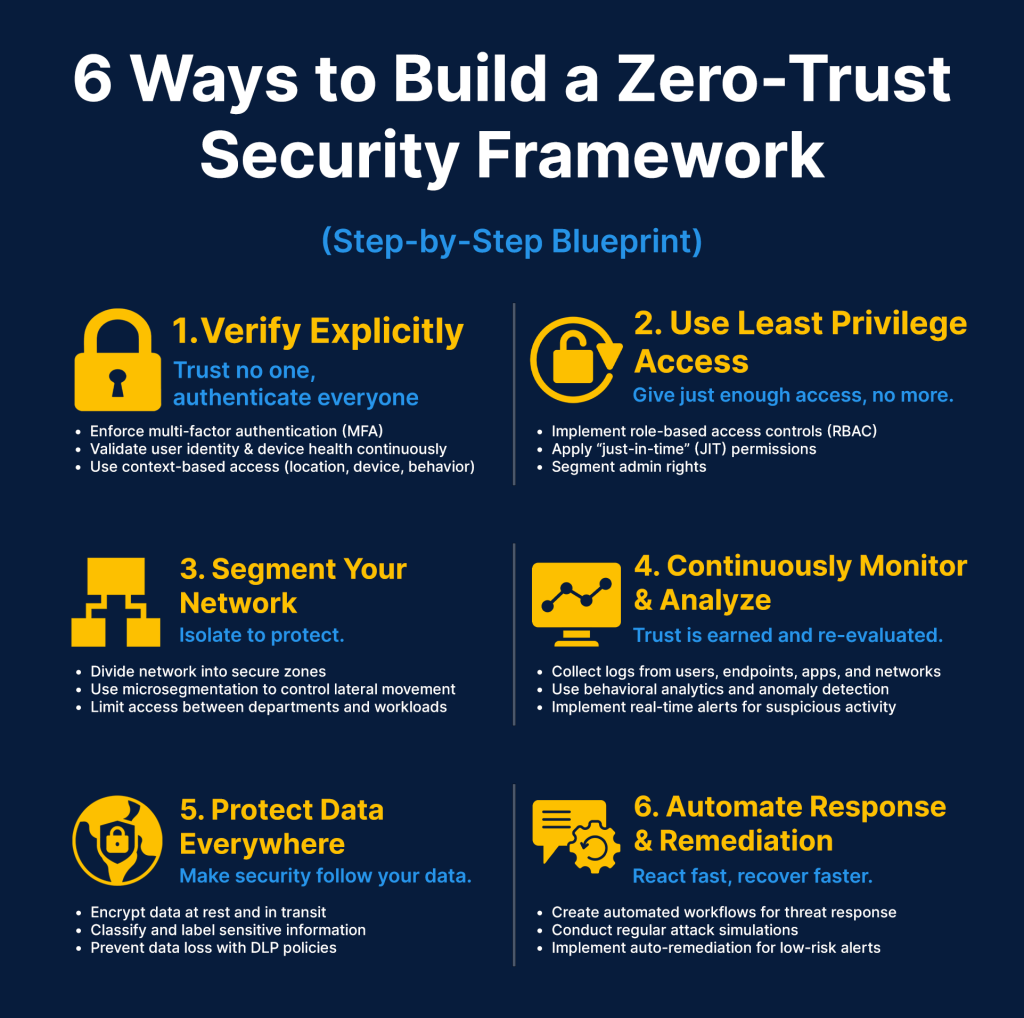
Securing the Remote Workplace: Building a Zero-Trust Framework
Zero-trust is the core of compliance protection in a remote workplace. Gartner’s report says that worldwide, 63% of organizations have successfully implemented a zero-trust framework. This shift is necessary to battle against evolving cyber threats.
Leveraging AI Technology to Reduce Compliance Risks in Remote Operations
Emerging technologies like Artificial Intelligence (AI) are fast becoming game-changers in protecting compliance in remote-first and hybrid operations. Instead of reacting to incidents after they occur, compliance leaders today seek solutions that help them anticipate, detect, and respond to risks in real-time.

wAnywhere is a pioneer in this space, offering AI-powered compliance and employee monitoring solutions that safeguard sensitive data, ensure policy adherence, and keep teams aligned with regulatory standards no matter where they work from.
Purpose-built for distributed teams, wAnywhere gives CISOs and COOs access to rich, actionable workforce analytics—from how employees handle sensitive data, to when and where anomalies arise in day-to-day operations. With real-time visibility into work patterns and behavior, leaders can detect hidden risks, identify gaps in compliance hygiene, and take proactive action—without disrupting productivity.
And beyond real-time threat detection, wAnywhere enables swift incident response to minimize damage, automate documentation, and support investigation workflows.
- Real-time compliance monitoring
- Detailed audit trails
- Insider threat detection
- Geo-location and device-based restrictions
- Mobile/Voice/Face detection
- Unknown/Multiple/No Person detection
- PHI/PII masking
- Custom screenshots
- Custom compliance dashboards
- Role-based access control (RBAC)
- AI-powered productivity analytics

Virtual Staffing Solutions Strengthened Compliance in Remote Operations with wAnywhere
99% adherence to Clean Desk Policy
73% increase in productivity
Full visibility into workforce behavior
Conclusion
Remote work culture is successful and sustainable only when compliance and data security are not compromised. That’s why C-suite leaders like CISOs and COOs play a very significant role to drive a culture where compliance is seen as a shared responsibility.
Safeguarding remote compliance policies is now a boardroom priority — one that can be managed through company-wide collaboration, strong leadership, and continuously evolving strategies.
In the coming times, as more and more businesses adopt a remote-first approach, data-related and compliance risks will also keep evolving. In such a situation, it is important for leaders to stay sharp and proactive.
By implementing continuous monitoring systems, automation workflows, and a robust culture of accountability, leaders can enhance the compliance, safety, and growth of remote businesses.

Strengthen Remote Compliance & Productivity with wAnywhere
FAQs
How To Ensure Remote Work Compliance
Remote work compliance can be ensured by implementing a mix of the right policy, technology, and culture in businesses. These three factors go hand in hand to help you achieve sustainable and audit-ready compliance.
Leverage technologies like employee and compliance monitoring tools for enhanced visibility into your employees’ activities at any time. Enforce secure access through VPNs and multi-factor authentication to ensure data protection standards like GDPR, HIPAA, ISO, etc., are followed. Conduct regular audits and compliance checks to identify security gaps and patterns. Finally, build a strong culture of accountability through ongoing training and awareness programs.
How can CISOs and COOs reduce compliance risk in remote teams?
CISOs and COOs can reduce compliance risks by working in tandem. CISOs should focus on implementing robust cybersecurity and monitoring systems, while COOs should ensure processes, communication, and training are aligned with compliance goals. Together, they can:
- Deploy real-time monitoring for suspicious activities
- Ensure data handling aligns with regulatory standards
- Build a culture that prioritizes compliance without micromanaging
What role does the COO play in managing compliance risk?
The COO ensures that compliance is embedded into operational workflows and team behaviors. A COO can manage compliance risks by designing scalable processes that align with regulations, conducting consistent training and communication, making compliance part of everyday operations, and coordinating with HR, IT, and security teams to enforce company-wide standards.
What role does the CISO play in managing compliance risk?
The CISO is the guardian of data security and regulatory alignment. Their role in managing compliance risks includes:
- Implementing secure infrastructure for remote work
- Monitoring potential security breaches or policy violations
- Ensuring systems and tools that meet compliance standards
- Advising the executive team on emerging risks and threat mitigation strategies








